July 10, 2025
Getting subscribers to open your emails may be difficult sufficient. You pour your coronary heart and soul into crafting the right marketing campaign solely to see it left unopened or worse, despatched straight to the spam folder. However what if the issue isn’t your content material or providing? It may very well be that subscribers merely don’t belief your model.
Constructing belief is important for profitable electronic mail advertising and marketing. When subscribers belief your model, they’re extra prone to open your emails, have interaction along with your content material, and convert into clients. However with the rise of spoofing, phishing scams, and different cyberattacks, customers are extra skeptical of emails than ever earlier than.
So, what to do about it? On this put up we’ll not solely focus on the largest elements that may erode subscriber belief, however how one can rebuild it and enhance your electronic mail advertising and marketing deliverability.
Steep rise in cyberattacks
The rise in spoofing, phishing, and different cyberattacks has had a big detrimental influence on model belief in a subscriber’s inbox. Simply have a look at the numbers. In 2019, an estimated 779,200 assaults have been noticed by the Anti-Phishing Work Group (APWG). Solely 4 years later, in 2023, that quantity jumped to over 5 million – a 541% improve.
What’s extra, an estimated 3.4 billion emails a day are despatched by cyber criminals designed to seem like they arrive from trusted senders (i.e., from you). That is over a trillion phishing emails per 12 months. Can you actually blame subscribers for being skeptical over the legitimacy of what lands of their inbox, even when it is from a trusted supply?
The primary drawback for manufacturers is the character of those assaults. Criminals use spoofing methods, the place they disguise their emails to seem as if they’re from a professional supply. As subscribers grow to be extra conscious of cyber threats, they’re prone to be extra cautious of emails they obtain, even from acquainted manufacturers. This could make it tough so that you can get your messages throughout and may result in subscribers deleting emails, marking them as spam, or just not opening them.
In case you are unfamiliar with fashionable cyber safety threats, right here’s an inventory of a number of the most typical assaults your clients face:
|
Cyberattack sort |
Summary |
|---|---|
|
Phishing |
An email phishing attack is a fraudulent attempt to steal a victim’s personal information through email. Phishers attempt to tricokay people into skinnyking the email is from a legitimate bitterce, such as a financial institution, credit card company, or a familiar online store. |
|
Whaling |
Unlike regular phishing which targets a larger audience, whaling specifically targets CEOs, CFOs, or other executives with access to sensitive informationrmation or financial resources. |
|
Spoofing |
Email spoofing is a common tactic used in phishing attacks, which intention to steal a victim’s information or infect their device. By disguising themselves as someone a victim trusts, attackers increase the chances of people falling for their rip-off. |
|
Smishing |
Smishing is a kind of cyberattack that makes use of textual content messages (SMS) to tricokay victims into giving away personal informationrmation or clicking on malicious hyperlinks. It’s basically phishing however accomplished through SMS instead of email. |
|
Pharming |
Pharming is a cyberattack that steals information by cleverly redirecting people to a pretend, identical copy of an actual website. |
|
Quishing |
A quishing attack is a cyberattack that leverages QR codes to tricokay victims into visiting malicious websites. |
Whereas phishing assaults can goal any business, there are specific elements which make explicit industries extra weak than others. For instance, small and medium companies (SMBs) sometimes have fewer sources to speculate in sturdy cybersecurity measures, making them extra engaging targets.
One other widespread goal is monetary establishments. Banks and credit score unions maintain delicate information comparable to account and social safety numbers – one other juicy possibility for attackers seeking to steal monetary info.
Right here’s an inventory of a number of the most attacked industries:
|
Industry |
Percentage |
|---|---|
|
Finance |
27.7% |
|
Other |
18.2% |
|
SaaS |
17.7% |
|
Social Media providers |
10.4% |
|
Logistics and shipping |
9% |
|
Payment services |
6% |
|
eCommerce and retail |
5.6% |
|
Telecom |
3.1% |
|
Cryptocurrency |
2.3% |
Information sourced from the APWG Phishing Exercise Traits Report
So, if your enterprise operates carefully in any of those sectors, it’s particularly necessary you’re taking steps to prioritize transparency and safety, implement sturdy authentication protocols, and stick with electronic mail advertising and marketing greatest practices to construct up belief along with your subscribers.
What may be accomplished to reassure subscribers?
Now you’ve seen why subscribers have a superb cause to be cautious of what lands of their inbox, let’s have a look at what you are able to do regain their confidence.
Implement electronic mail authentication protocols
E mail authentication is a set of protocols that work collectively to confirm the legitimacy of a sender. In easier phrases, it’s like a digital ID verify for emails. This verification course of helps construct belief in model communications by reassuring recipients that the e-mail was really despatched by the model, and never a malicious imposter.
The three customary electronic mail authentication protocols are:
- SPF (Sender Coverage Framework)
- DKIM (DomainKeys Recognized Mail)
- DMARC (Area-based Message Authentication, Reporting, and Conformance).
They work in conjunction to validate a sender’s id, forestall electronic mail spoofing and phishing assaults, and enhance general safety and electronic mail deliverability.
Let ’s have a look at each in somewhat extra element.
SPF – Sender Coverage Framework
SPF is sort of a listing you give to the put up workplace saying who’s allowed to ship mail in your behalf. Anybody on the listing (licensed electronic mail servers) can ship emails along with your identify on it (your area identify within the “From” handle).
If somebody not on the listing (unauthorized server) tries to ship an electronic mail pretending to be you, the put up workplace (receiving electronic mail server) will grow to be suspicious and received’t ship it to the recipient’s inbox.
DKIM – DomainKeys Recognized Mail
Think about you’re sending a signed, licensed letter. DKIM is like that for emails. Once you ship an electronic mail, DKIM provides a particular digital signature to your message. This signature is actually a secret code solely you and the recipient’s mailbox know.
The recipient’s mailbox can then verify this code with a public report to confirm it’s actually from you.
DMARC – Area-based Message Authentication Reporting and Conformance
Sticking with the put up workplace analogy, DMARC could be the set of directions on what to do with these unrecognized letters (i.e., those who fail SPF or DKIM). You possibly can inform them to bounce them again (reject), maintain them for inspection (quarantine), and even allow them to by (ship) with a warning label.
Educate subscribers about cyber threats
When you may not work straight within the cybersecurity subject, you possibly can nonetheless reassure subscribers by educating them about cyber threats and supply recommendations on the best way to safely navigate their inbox.
One other good observe is to stipulate precisely what delicate information you’d ask for through electronic mail (if in any respect), from which sender handle, and the way. This manner clients are higher knowledgeable on the best way to spot suspicious emails from attackers attempting to impersonate your model. Let’s have a look at an instance from Nationwide Constructing Society (monetary establishment).
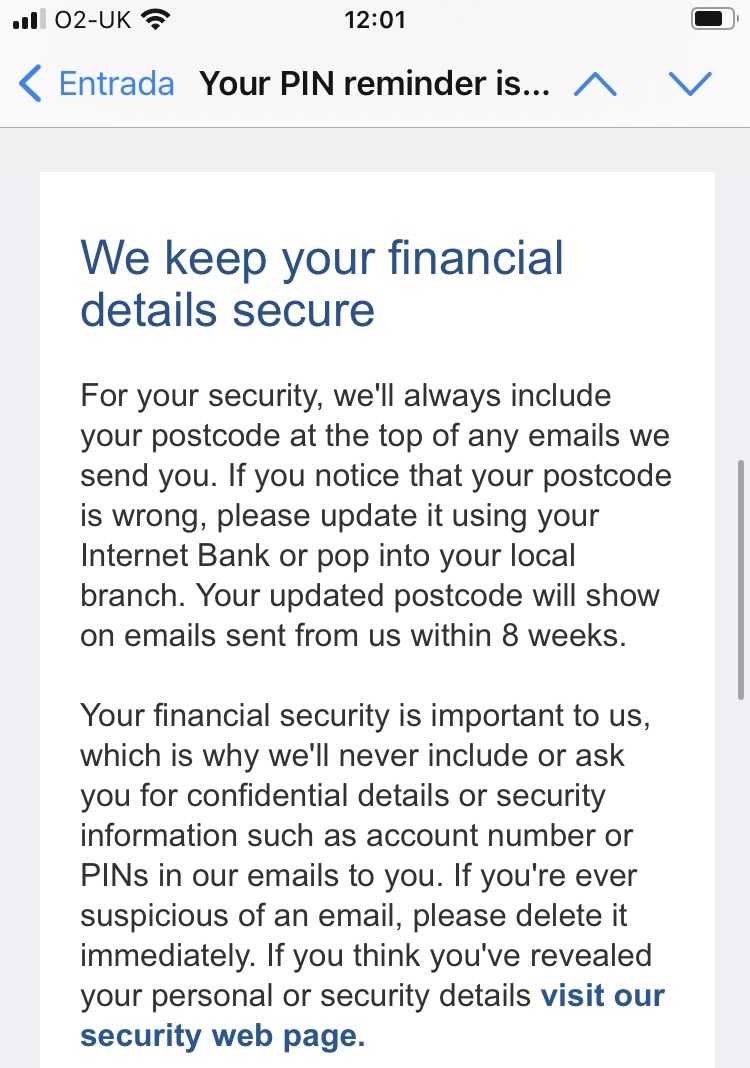

Discover how Nationwide present a hyperlink to a devoted safety internet web page if clients suspect any suspicious exercise.
The constructing society clearly outlines their coverage for delicate information assortment, informing clients that they’ll by no means embody or ask for confidential info through electronic mail. Subsequently, any correspondence of this nature acquired from the financial institution must be handled as fraudulent.
By being particular concerning the delicate information you accumulate and the way, manufacturers can construct belief with their clients and in the end create a safer surroundings for each themselves and subscribers.
Be clear and accountable
Earlier than the implementation of information regulation legal guidelines comparable to GDPR and the CAN-SPAM act, the e-mail advertising and marketing plains have been a just like the Wild West. Baron, lawless, and fraught with hazard.
Whereas that is likely to be a slight exaggeration, the shopper–model relationship undoubtedly turned strained. Subscriber’s felt their private information was being misused, with out their consent, to the monetary advantage of corporations. Whereas that has now been introduced beneath management – with manufacturers now held accountable for his or her information assortment insurance policies – scars from that bygone period stay.
So, what can manufacturers do about it? By taking steps to not solely abide by new information regulation insurance policies however overtly clear about what’s being collected and why, manufacturers can assist to rebuild belief with their subscribers and be certain that their electronic mail advertising and marketing efforts are profitable.
Prioritize electronic mail deliverability
Every single day, necessary emails containing password resets, particular presents, and important updates land in our subscribers’ inboxes. If they’re delayed, trapped in a spam filter, or vanish altogether buyer frustration mounts and their belief in your model begins to fade.
That’s why specializing in deliverability is an glorious technique to not solely improve model belief, but additionally increase your return on funding (ROI) from the e-mail channel. In truth, a 2023 Forrester Consulting Whole Financial Influence™ examine on our sister firm, Sinch Mailgun, discovered that organizations would see a 264% ROI improve after simply three years from improved electronic mail deliverability. Not unhealthy, proper?
And don’t simply take our phrase for it. Virtually a 3rd of customers from Sinch Mailgun’s 2024 E mail and Buyer Expertise report (32.8%) admitted they’d be irritated or pissed off if a model’s emails frequently find yourself in spam. One other 10% say they’d lose belief in your model, and virtually as many say they’d unsubscribe out of your emails.
Be constant
Constant electronic mail sending schedules create a way of routine. Subscribers know when to anticipate your emails and grow to be accustomed to seeing your model of their inbox. Which means, when you’ve caught to greatest practices and despatched a double opt-in affirmation the subscribers left in your electronic mail listing are there for a cause – they need to obtain your content material.
So, once you fail to point out up on time (or in any respect) they’re not going to be too greatest happy.
Consistency additionally goes past simply the timing and high quality of your emails. Sustaining a constant model voice, design aesthetic, and worth proposition throughout your emails reinforces your model id and builds belief. Subscribers come to acknowledge your model and perceive the worth you provide, fostering a way of familiarity and reliability. This consistency demonstrates that you just’re not simply out for a fast sale, however slightly dedicated to constructing a long-term relationship along with your viewers.
How can Sinch Mailjet assist?
At Sinch, electronic mail deliverability and authentication are on the core of our product providing for all our electronic mail options. We’re consistently striving to offer senders the instruments and recommendation wanted to determine belief with their viewers and maximize electronic mail marketing campaign efficiency.
When you’d like to search out out extra about how we can assist, drop us a line beneath. We sit up for listening to from you!


